A new report has revealed that three quarters of healthcare organisations in the UK and globally are at risk from cyber vulnerabilities, making the sector the worst affected across all industries.
The report, from Forescout Research Labs, discloses a number of serious Transmission Control Protocol (TCP) and Internet Protocol (IP) vulnerabilities found in healthcare devices.
And it found that healthcare organisations are five times more likely to be impacted by these threats than any other industry.
If exploited, these vulnerabilities can allow attackers to take target devices offline or take control of their operations, potentially causing widespread disruption.
The most-common vulnerable medical device types include infusion pumps, patient monitors, and point-of-care diagnostic systems.
Key findings
- 75% of healthcare organisations are affected by the TCP/IP vulnerabilities uncovered. These have on average per organisation, the highest number of vulnerable devices (almost 500), the highest diversity of vulnerable devices (eight device types) and the highest diversity of vulnerable vendors (12) on their networks
- Healthcare organisations are roughly five times more affected by TCP/IP vulnerabilities than any other vertical. There are, in total, 79 vulnerable types of devices and 259 vulnerable vendors
- The most-common vulnerable device types in healthcare organisations are printers, VoIP, infusion pumps, networking equipment, and building automation devices. The most-common vulnerable medical device types are infusion pumps, patient monitors and point-of-care diagnostic systems
- These and other vulnerable devices often share the same segments of an organisation’s network, which increases the potential likelihood and impact of cyber attacks
- The combination of new vulnerable devices, difficult-to-patch vulnerabilities, and lack of segmentation exposes healthcare networks to new threat scenarios that can have a big business impact
These findings shed light on the difficulties of managing cyber security in the IoT world.
In networks with high device diversity, security operators need to spend a considerable amount of time identifying and patching vulnerable devices.

The report warns of the most-common vulnerabilities within the health sector
This is because the tools able to identify IT devices might differ from those able to identify medical or IoT devices; and the different device types come from different vendors and hence patches are available on different timelines and applicable with different procedures.
And, since patches for TCP/IP stack vulnerabilities must trickle down the supply chain, several of those vendors either do not issue patches, or take months to do so, which means the affected devices remain vulnerable for a long period of time.
Furthermore, the combination of new vulnerable devices, difficult-to-patch vulnerabilities, and lack of network segmentation increases cyber risk, the potential likelihood, and impact of cyber attacks.
And this exposes healthcare networks to new threat scenarios that can have large business impact, including:
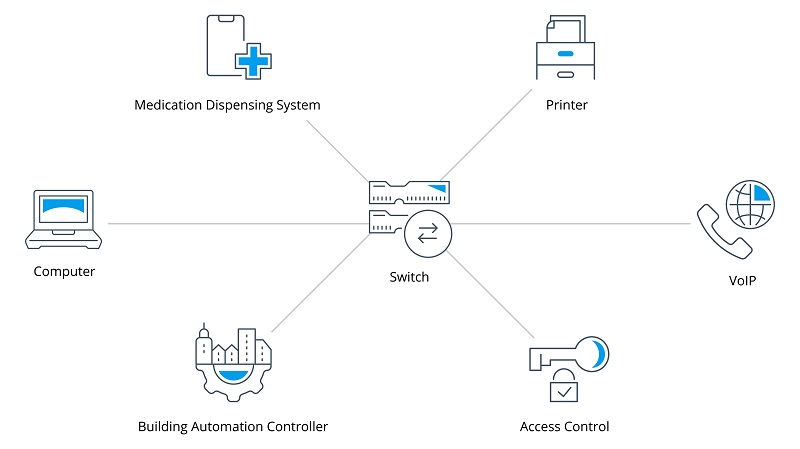
An example of vulnerable VLANs
- Increased exposure to attacks – since more devices and less monitored device types are now vulnerable, organisations are more susceptible than ever to cyber attacks that affect the confidentiality and availability of sensitive data. This comes at a time of rising costs associated to healthcare data breaches, which cost an average of $7.13m in 2020, which includes lost business because of customer turnover, damaged reputation, or system downtime
- Increased downtime of affected devices – ransomware can take big parts of an organisation offline, but it is now something that the industry has learned to deal with by following standard guidelines. Downtime caused by exploiting vulnerabilities in embedded devices can be much higher because it may affect different device types in a completely-different way (for example, network disconnection, intermittent downtime, and persistent denial of service), is mostly unknown to cybersecurity personnel, and may demand specialised maintenance from the vendor or, in the worst case, equipment replacement. At a cost of thousands of dollars per scan, plus idle staff, plus delayed patient care, each hour that an MRI scanner is down can easily cost tens of thousands in lost revenue
- Denial of healthcare delivery – previous attacks lead to reputational damage, due to data breaches, or a decrease in healthcare delivery capacity, due to ransomware, which translate into lost revenue. However, attacks targeting medical devices such as patient monitors and infusion pumps can completely stop the ability to provide patient care and, in the worst case, harm patients
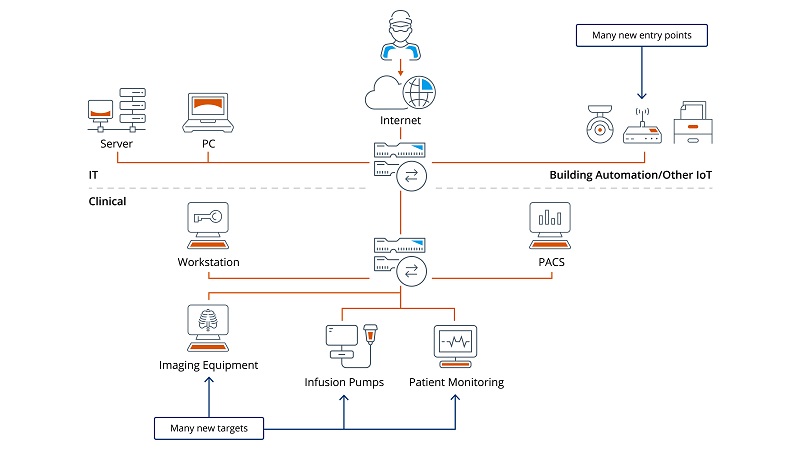
Emerging threat scenarios - the IoT threat
These IoT security challenges and emerging threat scenarios mean that every organisation, especially in the healthcare sector, needs a proactive and holistic approach to cyber security that prioritises the following steps:
- Discover and inventory devices running the vulnerable stacks and assess their business risk. Forescout Research Labs has released an open-source script that uses active fingerprinting to detect devices running the affected stacks. The script is updated constantly with new signatures to follow the latest development of the research
- Enforce segmentation controls and proper network hygiene to mitigate the risk from vulnerable devices. Restrict external communication paths and isolate or contain vulnerable devices in zones as a mitigating control if they cannot be patched or until they can be patched.
- Monitor progressive patches released by affected device vendors and devise a remediation plan for vulnerable asset inventory, balancing business risk and business continuity requirements
- Monitor all network traffic for malicious packets that try to exploit known vulnerabilities or possible 0-days affecting TCP/IP stacks. Anomalous and malformed traffic should be blocked, or at least alert its presence to network operators




